Taking Identity Management Seriously – Preventing Identity Theft
06 March 2020 00:00 by Dawid Jacobs
- Legal
- Law and Technology
- IT and Data Protection
- identity management
- LegalTech
- KYC
- identity fraud
- personal information
By Dawid Jacobs
Identity Management Specialist, on behalf of LexisNexis South Africa
Taking Identity Management Seriously – Preventing Identity Theft
“Identity theft, criminal investigations of the dead or missing, mass disasters both by natural causes and by criminal intent – with this as our day to day reality, the establishment and verification of human identity has never been more important or more prominent in our society. Maintaining and protecting the integrity of our identity has reached levels of unprecedented importance and has led to international legislation to protect our human rights.” – (Forensic Human Identification: An Introduction, 1st Edition - Tim Thompson, Sue Black)
Identity theft and identity fraud have been escalating unabated year on year. Identity thieves are harvesting identities and personal information, yet we see very little of this harvested information being used currently in criminal activities, which points to it being used in Sybil-like attacks in the near future.
The Sybil attack in computer security is an attack wherein a reputation system is subverted by forging identities in peer-to-peer networks. It is named after the subject of the book Sybil, a case study of a woman diagnosed with dissociative identity disorder.
Current identity protection solutions
With the ever-increasing demand,need and hype to provide a Digital Identity (DID) and/or Self-sovereign identity (SSI) for everyone globally, there has been an explosion of identity management solutions service providers who create a DID or SSI or both, for anyone who enrols or registers themselves onto their platforms. As a result, many institutions are offering identity protection to their clients via these identity protection solutions when they self-register.
Inherent problems to the solutions
As elaborate as the solutions are, they are more than likely increasing the risk of being infiltrated by crime syndicates using fraudulent and synthetic identities to commit crime. Why? Most digital identities and SSIs are created by allowing individuals to self-register their identity onto their platform by using facial recognition, voice recognitionand personally identifiable information (PII).
Upon enrolment, these solutions match the face (selfie) of the individual subject to any ‘trusted’ document the subject presents as proof of identity. Consider the fact that over 7.7 billion people live on earth and each could potentially have ten DDIs and even SSIs, as many as they please, without actually being linked to them. How is this possible?
Firstly Biometrics (as a trusted source) is improving, but so is the spoofing thereof. Consider:
- Image falsification: Imagine the scenario presented by https://thispersondoesnotexist.com/ which generates a shockingly realistic — but totally fake — picture of a person’s face every time the site is refreshed. Every photo on the site has been created by using a special kind of artificial intelligence algorithm called generative adversarial networks (GANs).
- Voice falsification: https://soundcloud.com/alexismadrigal/google-duplex-calling-a-restaurant - in which Google Duplex, mimicking a human voice, books a restaurant table with the help of Google Assistant.
And then ask yourself how good this technology will be in two years’ time.
Secondly the threat increases drastically if – in light of criminal syndicates virtually having carte blanche to create as many fraudulent identities and synthetic identities as they please – there could be billions of ’identities’ which do not even belong to any human.
This allows us to conclude the following with relative certainty:
- ‘Trusted’ sources have already been compromised.
- NO adequate proof of any evidence exists in current solutions of an irrefutable forensic link between individual human beings and their corresponding identity as created on these ‘selfie identity management solutions’.
- The risk of fraudulent identities and synthetic identities being created on these platforms is enormous and they cannot prove that an authentication corresponds 100% to the claimed Identity.
Yet, this situation continues to go relatively unnoticed. All of which is further compounded by the exponential growth in the speed and complexity of digital identities, self-sovereign identities, artificial intelligence, tokenization and the internet of things as evidenced by Moore’s Law and other studies.
Masses of complexity, threatening a single truth:You are either 100% you, or 0% someone else - NO grey area should exist in identity management.
Addressing the problem
True identity protection and authenticationis based on the collection of the evidence that only one ‘real-world human being’ exists who can lay claim to one specific Identity.
A Forensic Protocol must be usedduring the collection/registration/enrolment of an identity onto any system as it is of the utmost importance to enable 100% authentication of the identity at any stage thereafter.
Authentication process: The attribute or markings belonging to a specific human being must be collected with a forensic protocol. Thus, the human being’s attributes or markings, must:
- be collected at a specific (and recordable) time and place;
- be accepted as forensic evidence;
- be captured/registered/collected by and in the presence of an authorised person eligible to perform this function;
- be captured/registered/collected with a strict chain of custody protocol; and
- contain all relevant personal information of the individual identity as presented to the authorised person upon capturing/registration/collection of claimed identity.
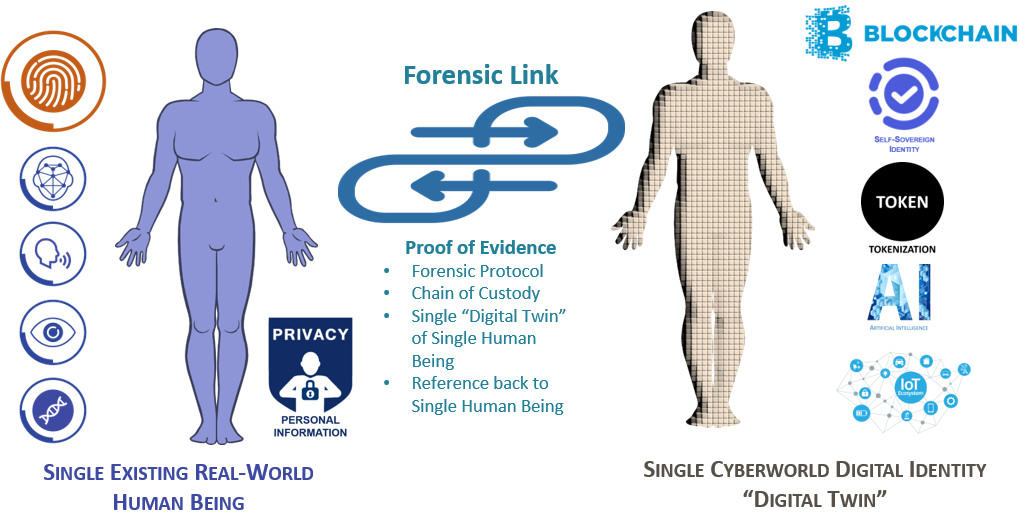
To ensure that the physical world, or real world as we know it keeps up with the digital or cyber world, the existence of every single individual real-world human being must be recognised as core to any identity in the cyber world. It is therefore essential for a subject human being to be linked to a corresponding single cyber world digital identity with the forensic protocol.
In essence, a single digital identity MUST therefore be a ‘single digital twin’’of its corresponding single human being, and in so doing allow for accurate identity authentication of the human in all spheres of the cyber world, as illustrated in the following image - supplied by https://www.dal-global.co.za/.
Since all personal information relating to a single identity can now be linked with certainty:
- SSI will be optimised and relevant and truly accepted as being that of one individual identity. The SSI presented or owned can be claimed and verified as it will have a reference to a single human being.
- Problems related to identities in RegTech and on Blockchain (Cryptocurrencies and Tokens) will be solved.
- Any potential criminal activity will not only be prevented, but also result in proof of evidence if any wrongdoing is committed – as reference back to a human will be 100% secure.
- Synthetic identities will be nullified
Conclusion
It is time to take identity management seriously and to recognise that an identity is proof that evidence of a single existing real-world human being exists and that this evidence must always be collected and treated with forensic protocol.
Related Posts
-
 06 March 2020 00:00 by Dawid JacobsSynthetic identity theft, or rather synthetic identity creation, has become a major breakthrough for fraudsters. The days of having to find a ‘mark’ with a good credit standing who ticks all the boxes for stealing their identity in order to defraud financial and other institutions, are fast disappearing. Syndicates have evolved in their methods of theft and fraud, safe in the knowledge that they can neither be identified, nor caught, and never be prosecuted.
06 March 2020 00:00 by Dawid JacobsSynthetic identity theft, or rather synthetic identity creation, has become a major breakthrough for fraudsters. The days of having to find a ‘mark’ with a good credit standing who ticks all the boxes for stealing their identity in order to defraud financial and other institutions, are fast disappearing. Syndicates have evolved in their methods of theft and fraud, safe in the knowledge that they can neither be identified, nor caught, and never be prosecuted. -
 06 March 2020 00:00 by Dawid JacobsSynthetic identity theft, or rather synthetic identity creation, has become a major breakthrough for fraudsters. The days of having to find a ‘mark’ with a good credit standing who ticks all the boxes for stealing their identity in order to defraud financial and other institutions, are fast disappearing. Syndicates have evolved in their methods of theft and fraud, safe in the knowledge that they can neither be identified, nor caught, and never be prosecuted.
06 March 2020 00:00 by Dawid JacobsSynthetic identity theft, or rather synthetic identity creation, has become a major breakthrough for fraudsters. The days of having to find a ‘mark’ with a good credit standing who ticks all the boxes for stealing their identity in order to defraud financial and other institutions, are fast disappearing. Syndicates have evolved in their methods of theft and fraud, safe in the knowledge that they can neither be identified, nor caught, and never be prosecuted.
 Lexis Nexis
Lexis Nexis